Beware of the Remote Code Execution Scam! Recently, some clients of Nustart Solutions got a tricky scam email. It talks about a “Remote Code Execution (RCE)” issue and tells you to download a patch by clicking a button. But be careful—it’s a phishing scam!
This scam is cleverly designed to look official and urgent, but it’s all a trick. The goal is to get you to click on the link, which doesn’t lead to a legitimate WordPress site or plugin. Instead, it might take you to a fake website where your information can be stolen, or it could cause you to download malware onto your computer.
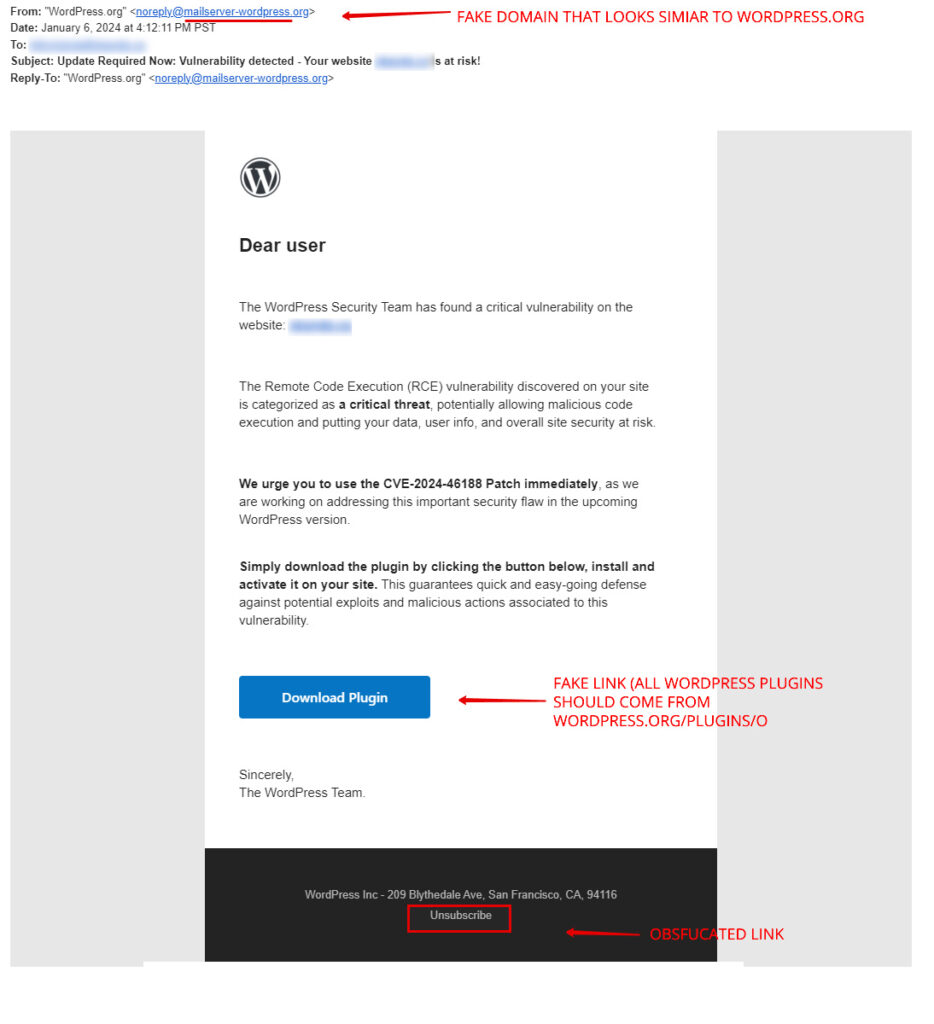
Here’s how you can tell this email is a Remote Code Execution Scam:
- The email might look like it’s from “WordPress.org” at first glance, but the real address is different. It’s from “mailserver-wordpress.org,” which was only set up 20 days ago.
- The “Download Plugin” button doesn’t take you to the official WordPress plugin site. Instead, it uses a bit.ly link, which hides the real destination.
- Think about it—why would you get a plugin through an email? You should always update plugins right from your WordPress dashboard.
- Even the unsubscribe button links to a bit.ly URL, so you can’t be sure what it really does.
What to do if you receive this Remote Code Execution Scam email:
Don’t click any links in the email. It’s best to mark it as spam and block the sender, or just delete the email.
What is an Email Phishing Scam?
Email phishing scams are a serious threat in today’s digital world. These scams involve sending deceptive emails to trick recipients into revealing sensitive information, such as passwords or credit card numbers. The scammer often pretends to be from a reputable company, like a bank or an internet service provider, to gain the victim’s trust.
Phishing emails can look very convincing. They often use official logos and familiar formatting. However, there are usually signs that something is not right. For example, the email might have spelling mistakes or awkward language. It might also use a generic greeting, like “Dear Customer,” instead of your name.
One common tactic in phishing emails is to create a sense of urgency. The email might say that your account has been compromised and you need to update your password immediately. Or it could claim that you’ve won a prize and need to provide personal information to claim it. These tactics are designed to make you act without thinking.
Another red flag is if the email asks you to click on a link or download an attachment. These links or attachments can lead to fake websites designed to steal your information, or they might install malware on your computer.
To protect yourself from phishing scams, always be cautious with unsolicited emails. Don’t click on links or download attachments from unknown sources. If you’re unsure about an email, contact the company directly using a phone number or website you know is legitimate.
Remember, reputable companies will never ask for sensitive information through email. If you receive an email asking for this kind of information, it’s likely a phishing scam. Always report suspicious emails to your email provider and the company being impersonated.
Sadly, this isn’t the only scam email out there. Be suspicious of any emails about your website, WordPress, or Sendgrid. Always check the “from” address carefully. If something seems off, forward the email to your hosting provider for help. Or, send it to anne+pleasecheck@nustart.solutions, and I’ll give you a second opinion.
In conclusion, email phishing scams are a significant threat, but by staying vigilant and understanding the signs, you can protect yourself and your information.
